 rhino.fi
rhino.fi
$39.08 M
4.25%
...
Choose token
 Ether (ETH)
Ether (ETH) Tether USD (USDT)
Tether USD (USDT) DeversiFi Token (DVF)
DeversiFi Token (DVF) Wrapped BTC (WBTC)
Wrapped BTC (WBTC) USD Coin (USDC)
USD Coin (USDC) Wrapped liquid staked Ether 2.0 (wstETH)
Wrapped liquid staked Ether 2.0 (wstETH) Matic Token (MATIC)
Matic Token (MATIC) Lido DAO Token (LDO)
Lido DAO Token (LDO) Dai Stablecoin (DAI)
Dai Stablecoin (DAI) Hermez Network Token (HEZ)
Hermez Network Token (HEZ) Uniswap (UNI)
Uniswap (UNI) Maker (MKR)
Maker (MKR) Blur (BLUR)
Blur (BLUR) Aave Token (AAVE)
Aave Token (AAVE) ChainLink Token (LINK)
ChainLink Token (LINK)...
Rebranding
2022 Jul 13th
DeversiFi becomes rhino.fi: multi-chain platform gathering DeFi in one place.
DeversiFi Relaunched using Starkware
2020 Jun 3rd
DeversiFi is live, bringing first STARKex Validium for spot trading.
Funds can be stolen if
Funds can be lost if
Users can be censored if
MEV can be extracted if
State validation
ZK proofs (ST)zkSTARKS are zero knowledge proofs that ensure state correctness.
Data availability
External (DAC)Proof construction relies fully on data that is NOT published on chain. There exists a Data Availability Committee (DAC) with a threshold of 4/7 that is tasked with protecting and supplying the data.
Exit window
NoneThere is no window for users to exit in case of an unwanted upgrade since contracts are instantly upgradable. Users can be explicitly censored from withdrawing (Blocklist on L1).
Sequencer failure
Force via L1Users can force the sequencer to include a withdrawal transaction by submitting a request through L1. If the sequencer censors or is down for for more than 7d, users can use the exit hatch to withdraw their funds.
Proposer failure
Use escape hatchUsers are able to trustlessly exit by submitting a Merkle proof of funds.
Validity proofs ensure state correctness
Each update to the system state must be accompanied by a ZK proof that ensures that the new state was derived by correctly applying a series of valid user transactions to the previous state. These proofs are then verified on Ethereum by a smart contract. The system state is represented using Merkle roots.
Zero knowledge STARK cryptography is used
Despite their production use zkSTARKs proof systems are still relatively new, complex and they rely on the proper implementation of the polynomial constraints used to check validity of the Execution Trace.
Funds can be lost if the proof system is implemented incorrectly.
Data is not stored on chain
The balances of the users are not published on-chain, but rather sent to external trusted parties, also known as committee members. A state update is valid and accepted on-chain only if at least a quorum of the committee members sign a state update.
Funds can be lost if the external data becomes unavailable (CRITICAL).
Users can be censored if the committee restricts their access to the external data.
The system has a centralized operator
The operator is the only entity that can propose blocks. A live and trustworthy operator is vital to the health of the system. Typically, the Operator is the hot wallet of the StarkEx service submitting state updates for which proofs have been already submitted and verified.
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force exit the system
Force exit allows the users to escape censorship by withdrawing their funds. The system allows users to force the withdrawal of funds by submitting a request directly to the contract on-chain. The request must be served within a defined time period. If this does not happen, the system will halt regular operation and permit trustless withdrawal of funds.
Users can be censored if the operator refuses to include their transactions. However, there exists a mechanism to independently exit the system.
Regular exit
The user initiates the withdrawal by submitting a regular transaction on this chain. When the block containing that transaction is proven the funds become available for withdrawal on L1. Finally the user submits an L1 transaction to claim the funds. This transaction does not require a merkle proof.
Forced exit
If the user experiences censorship from the operator with regular exit they can submit their withdrawal requests directly on L1. The system is then obliged to service this request. Once the force operation is submitted and if the request is serviced, the operation follows the flow of a regular exit.
Emergency exit
If the enough time deadline passes and the forced exit is still ignored the user can put the system into a frozen state, disallowing further state updates. In that case everybody can withdraw by submitting a merkle proof of their funds with their L1 transaction.
Blocklist
The BlockAdmin (see Permissions section) can add addresses to a Blocklist, preventing the finalization of their withdrawal on L1. This effectively locks the blocked party’s funds in the bridge escrow on L1 if the withdrawal had already been initiated on L2. The Blocklist is also effective on forced withdrawals.
Users can be censored if their address gets added to the Blocklist by the BlockAdmin.
The system uses the following set of permissioned addresses:
Can upgrade the implementation of the system, potentially gaining access to all funds stored in the bridge. Currently there is 3d delay before the upgrade.
Has full power to upgrade the bridge implementation as a Governor. This is a Gnosis Safe with 4 / 6 threshold.
Those are the participants of the GovernanceMultisig.
Validity proof must be signed by at least 4 of these addresses to approve state update.
Can upgrade implementation of SHARP Verifier, potentially with code approving fraudulent state. Currently there is 0s delay before the upgrade.
SHARP Verifier Governor. This is a Gnosis Safe with 2 / 3 threshold.
Those are the participants of the SHARPVerifierGovernorMultisig.
Allowed to update the state of the system. When the Operator is down the state cannot be updated.
Is the BlockAdmin: Can add addresses to a blocklist in the bridge, blocking the finalization of their withdrawals on L1.
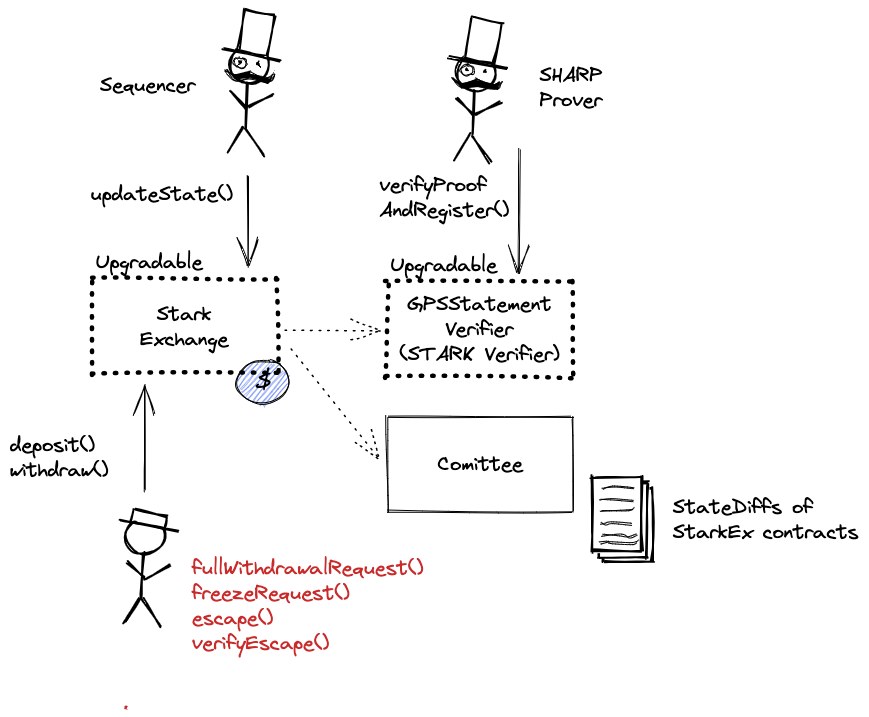
The system consists of the following smart contracts:
This contract can store any token.
Data Availability Committee (DAC) contract verifying data availability claim from DAC Members (via multisig check).
CallProxy for GpsStatementVerifier.
Starkware SHARP verifier used collectively by Starknet, Sorare, ImmutableX, Apex, Myria, rhino.fi and Canvas Connect. It receives STARK proofs from the Prover attesting to the integrity of the Execution Trace of these Programs including correctly computed state root which is part of the Program Output.
Part of STARK Verifier.
Part of STARK Verifier.
Part of STARK Verifier.
MemoryPageFactRegistry is one of the many contracts used by SHARP verifier. This one is important as it registers all necessary on-chain data.
Same as MemoryPageFactRegistry but stores facts proved by the old SHARP Verifier, used as a fallback.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).



