Search
Search for projects by name
 Zk.Money v2 (Aztec Connect)
Zk.Money v2 (Aztec Connect)
Badges
About
Aztec Connect is an open source layer 2 network that aims to enable affordable, private crypto payments via zero-knowledge proofs.
Tokens breakdown
Value secured breakdown
About
Aztec Connect is an open source layer 2 network that aims to enable affordable, private crypto payments via zero-knowledge proofs.
2022 Jun 08 — 2025 Jul 18
The section shows the operating costs that L2s pay to Ethereum.
2023 May 01 — 2024 Apr 09
Introducing Noir
2022 Oct 6th
Noir - programming language for zero-knowledge proofs, has been introduced.
SNARKs are zero knowledge proofs that ensure state correctness, but require trusted setup.
All of the data needed for proof construction is published on Ethereum L1.
Users can exit funds at any time because contracts are not upgradeable.
All data required for proofs is published onchain
Since EOL this is only true if the user themself runs the rollup locally and publishes the data.
The entire stack’s source code is housed in a single monorepo, which can be found here. For instructions on running the node, please refer to this readme. Since EOL the aztec-connect-ejector can be used to run a rollup instance and withdraw.
No compression is used.
The code to decode onchain data can be found here
Each update to the system state must be accompanied by a ZK proof that ensures that the new state was derived by correctly applying a series of valid user transactions to the previous state. These proofs are then verified on Ethereum by a smart contract.
No operator
EOL: Manual withdrawal using Aztec Connect Ejector
EOL: Aztec team announced they are going to shut down the rollup infrastructure on March 31st, 2024. Deposits are disabled and ownership of the rollup contract is irrevocably renounced. Assets in the escrow can be manually withdrawn with the Aztec Connect Ejector.
Regular withdraw (disabled)
Payments are private
Balances and identities for all tokens on the Aztec rollup are encrypted. Each transaction is encoded as a zkSNARK, protecting user data.
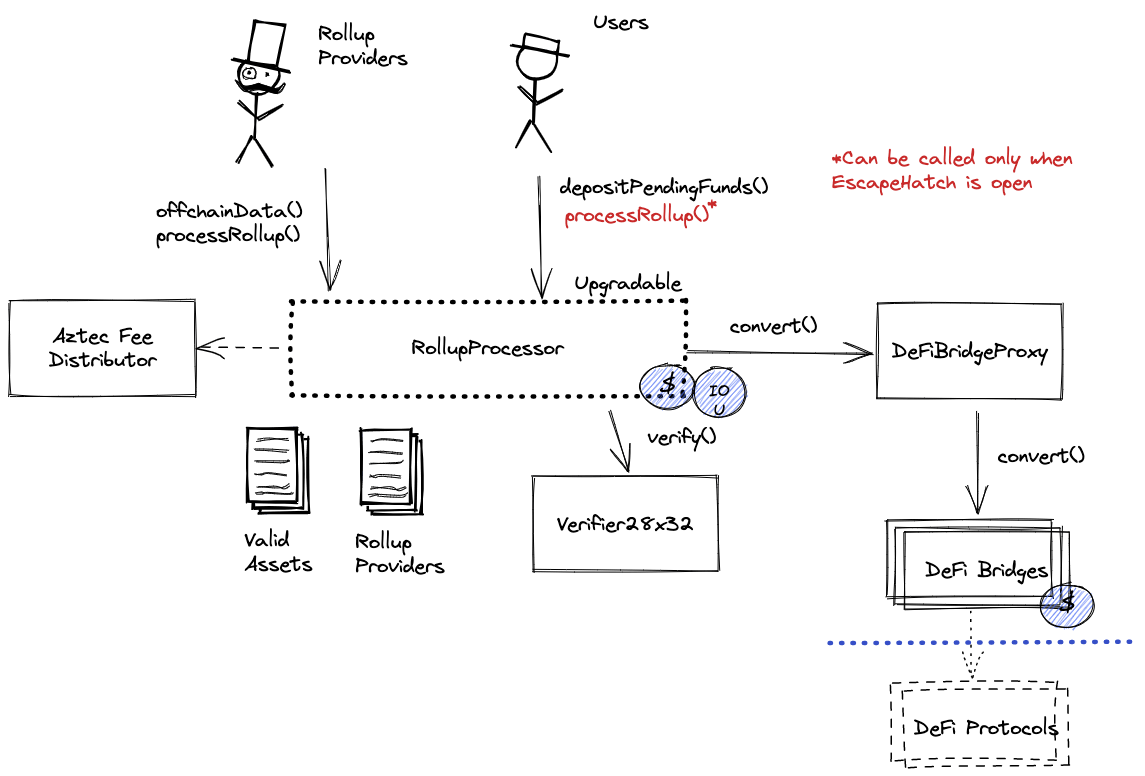
Ethereum
Main Rollup contract (immutable) responsible for withdrawals and accepting transaction batches alongside a ZK proof.
- This contract stores the following tokens: ETH, DAI, wstETH.
Bridge Connector to various DeFi Bridges.
Standard Plonk zkSNARK Verifier.