Search
Search for projects by name or address
 Fraxtal
Fraxtal
Badges
About
Fraxtal is an EVM equivalent Optimium utilizing the OP stack as its smart contract platform and execution environment.
Badges
About
Fraxtal is an EVM equivalent Optimium utilizing the OP stack as its smart contract platform and execution environment.
Why is the project listed in others?
Consequence: projects without a proper proof system fully rely on single entities to safely update the state. A malicious proposer can finalize an invalid state, which can cause loss of funds.
Consequence: projects without a data availability bridge fully rely on single entities (the sequencer) to honestly rely available data roots on Ethereum. A malicious sequencer can collude with the proposer to finalize an unavailable state, which can cause loss of funds.
Learn more about the recategorisation here.
2025 Mar 01 — 2026 Mar 01
The section shows the operating costs that L2s pay to Ethereum.
2025 Mar 01 — 2026 Mar 01
This section shows how "live" the project's operators are by displaying how frequently they submit transactions of the selected type. It also highlights anomalies - significant deviations from their typical schedule.
Funds can be stolen if
Funds can be lost if
Funds can be frozen if
MEV can be extracted if
Currently the system permits invalid state roots. More details in project overview.
Proof construction and state derivation rely fully on data that is NOT published on chain. Fraxtal uses a separate data availability module developed by the Frax Core Team, and data availability attestations are not published on chain.
There is no window for users to exit in case of an unwanted regular upgrade since contracts are instantly upgradable.
Only the whitelisted proposers can publish state roots on L1, so in the event of failure the withdrawals are frozen.
FraxtalDA is a custom data availability solution built by the Fraxtal team.
There are no onchain assets at risk of being slashed in case of a data withholding attack, and the committee members are not publicly known.
There is no fraud detection mechanism in place. A data withholding attack can only be detected by nodes downloading the full data from the DA layer.
Architecture
FraxtalDA is a custom data availability solution built by the Fraxtal team. The data is posted by the OP batcher to three separate locations: AWS, IPFS, and Cloudflare R2. The IPFS hash is then submitted to the onchain inbox contract on Ethereum. FraxtalDA relies on a single DA endpoint to manage data posting between the three different locations.

The sequencer attests to data availability by posting an IPFS hash to an onchain inbox contract on Ethereum. L2 nodes derive the L2 chain from the L1 by reading transactions commitments from this sequencer inbox. When reading from the inbox, the op-node verifies that the commitment hash is a valid IPFS CID. If the data corresponding to the hash is missing from IPFS, the op-node will halt, preventing further derivation of the L2 chain.
DA Bridge
The SequencerInbox only stores IPFS hash commitments posted by the sequencer. It is not possible to verify blob inclusion against the data commitments onchain. Projects not integrating with a functional DA bridge rely only on the data availability attestation of the sequencer.There is no committee attesting to the availability of the data. For L2 chain derivation, the system relies on sequencer commitments to an L1 onchain inbox. See DA layer technology section for more details.
Funds can be lost if the sequencer posts an invalid data availability commitment.
OP Stack projects can use the OP fault proof system, already being deployed on some. This project though is not using fault proofs yet and is relying on the honesty of the permissioned Proposer and Challengers to ensure state correctness. The smart contract system permits invalid state roots.
Funds can be stolen if an invalid state root is submitted to the system (CRITICAL).
The system has a centralized operator
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force any transaction
Because the state of the system is based on transactions submitted on the underlying host chain and anyone can submit their transactions there it allows the users to circumvent censorship by interacting with the smart contract on the host chain directly.
Regular messaging
Funds can be frozen if the centralized validator goes down. Users cannot produce blocks themselves and exiting the system requires new block production (CRITICAL).
Forced messaging
If the user experiences censorship from the operator with regular L2->L1 messaging they can submit their messages directly on L1. The system is then obliged to service this request or halt all messages, including forced withdrawals from L1 and regular messages initiated on L2. Once the force operation is submitted and if the request is serviced, the operation follows the flow of a regular message.
EVM compatible smart contracts are supported
OP stack chains are pursuing the EVM Equivalence model. No changes to smart contracts are required regardless of the language they are written in, i.e. anything deployed on L1 can be deployed on L2.

Ethereum
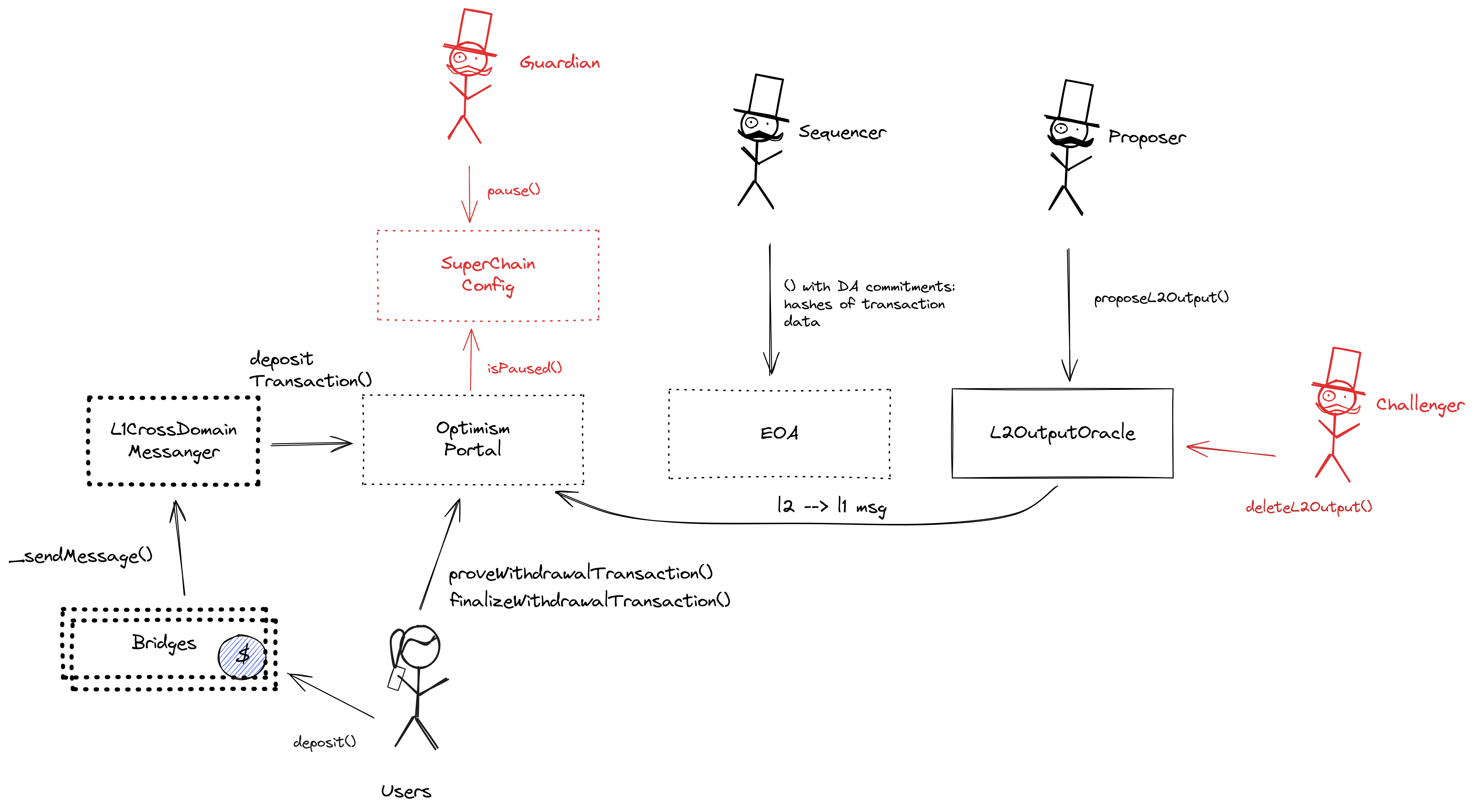
Roles:
Allowed to challenge or delete state roots proposed by a Proposer.
Allowed to pause withdrawals. In op stack systems with a proof system, the Guardian can also blacklist dispute games and set the respected game type (permissioned / permissionless).
Allowed to post new state roots of the current layer to the host chain.
Allowed to commit transactions from the current layer to the host chain.
Actors:
A Multisig with 3/5 threshold.
- Can upgrade with no delay
- OptimismMintableERC20Factory ProxyAdmin
- L1CrossDomainMessenger ProxyAdmin
- SystemConfig ProxyAdmin
- L1StandardBridge ProxyAdmin
- OptimismPortal ProxyAdmin
- SuperchainConfig ProxyAdmin
- L2OutputOracle ProxyAdmin
- L1ERC721Bridge ProxyAdmin
- Can interact with SystemConfig
- Can interact with AddressManager
- set and change address mappings ProxyAdmin
- A Challenger - acting directly
- A Guardian - acting directly
A Multisig with 3/5 threshold.
- Can interact with OptimismPortal
- Can interact with Frax Ether Token
- can add and remove frxETH minters and set a new timelock address with 2d delay FrxEthTimelock with 2d delay
- Can interact with frxETH Minter
- can withdraw all escrowed ETH, pause the contract and set user fees for minting frxETH (
submit()) with 2d delay FrxEthTimelock with 2d delay
- can withdraw all escrowed ETH, pause the contract and set user fees for minting frxETH (
Accepts user-supplied ETH to convert it to frxETH using auxiliary contracts like the EtherRouter.
- Can interact with Frax Ether Token
- can mint frxETH tokens
A Multisig with 4/7 threshold.
- Can interact with EtherRouter
- set the default AMO and lending pool contracts among the registered ones and trigger the predefined rebalancing functions of the router
- withdraw all escrowed ETH and ERC-20s and configure important addresses like the operator, AMO(s) or the lending pool(s)
- Can interact with frxETH Minter
- configure important addresses like the operator or the EtherRouter and withdraw ETH and ERC-20s from the contract (usually not escrowed here)
- pause ETH deposits / frxETH mints and withdraw ETH and ERC-20s from the contract (usually not escrowed here)
Accepts user-supplied ETH and converts it to frxETH.
- Can interact with Frax Ether Token
- can mint frxETH tokens
- A Proposer - acting directly
- A Sequencer - acting directly

Ethereum
The main entry point to deposit funds from host chain to this chain. It also allows to prove and finalize withdrawals.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
- frax_comptroller: Fraxtal Multisig 2
- guardian: Fraxtal Multisig 1
- This contract stores the following tokens: ETH, frxETH, FRAX.
Contains a list of proposed state roots which Proposers assert to be a result of block execution. Currently only the PROPOSER address can submit new state roots.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
- challenger: Fraxtal Multisig 1
- proposer: EOA 1
This is NOT the shared SuperchainConfig contract of the OP stack Superchain but rather a local fork. It manages the PAUSED_SLOT, a boolean value indicating whether the local chain is paused, and GUARDIAN_SLOT, the address of the guardian which can pause and unpause the system.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
- guardian: Fraxtal Multisig 1
Sends messages from host chain to this chain, and relays messages back onto host chain. In the event that a message sent from host chain to this chain is rejected for exceeding this chain’s epoch gas limit, it can be resubmitted via this contract’s replay function.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
The main entry point to deposit ERC20 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
- This contract can store any token.
Used to bridge ERC-721 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
A helper contract that generates OptimismMintableERC20 contracts on the network it’s deployed to. OptimismMintableERC20 is a standard extension of the base ERC20 token contract designed to allow the L1StandardBridge contracts to mint and burn tokens. This makes it possible to use an OptimismMintableERC20 as this chain’s representation of a token on the host chain, or vice-versa.
- Roles:
- admin: ProxyAdmin; ultimately Fraxtal Multisig 1
- Roles:
- owner: Fraxtal Multisig 1
ETH deposited by users via the FraxEtherMinter is forwarded to this contract and then routed further to either lending pools or AMOs.
- Roles:
- operatorAddress: Frax Multisig
- timelockAddress: Frax Multisig
frxETH token contract. Fraxtal uses Frax Ether as the designated gas token, allowing users to pay for blockspace with frxETH.
- Roles:
- minters_array: frxETH Minter
- timelock_address: FrxEthTimelock; ultimately Fraxtal Multisig 2
Allows for time-delayed execution of transactions. Current delay is 2d.
- Roles:
- admin: Fraxtal Multisig 2
Vault token contract (ERC-4626) for staked frxETH. The smart contract receives frxETH tokens and mints sfrxETH tokens.
Value Secured is calculated based on these smart contracts and tokens:
Main entry point for users depositing ERC20 token that do not require custom gateway.
Main entry point for users depositing ETH, frxETH, FRAX.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
