Search
Search for projects by name or address
 Morph
Morph
Badges
About
Morph is an EVM compatible rollup. It operates as an optimistic rollup with ZK fault proofs and has plans for decentralizing the Sequencer. Their mission is to build the first blockchain for consumers, where user-friendly applications integrate seamlessly... into everyday life, becoming indispensable utilities.
Badges
About
Morph is an EVM compatible rollup. It operates as an optimistic rollup with ZK fault proofs and has plans for decentralizing the Sequencer. Their mission is to build the first blockchain for consumers, where user-friendly applications integrate seamlessly... into everyday life, becoming indispensable utilities.
2025 Mar 08 — 2026 Mar 08
This section shows how much data the project publishes to its data-availability (DA) layer over time. The project currently posts data to![]() Ethereum.
Ethereum.
2025 Mar 08 — 2026 Mar 08
Funds can be stolen if
Funds can be frozen if
Users can be censored if
MEV can be extracted if
There is no mechanism to have transactions be included if the sequencer is down or censoring.
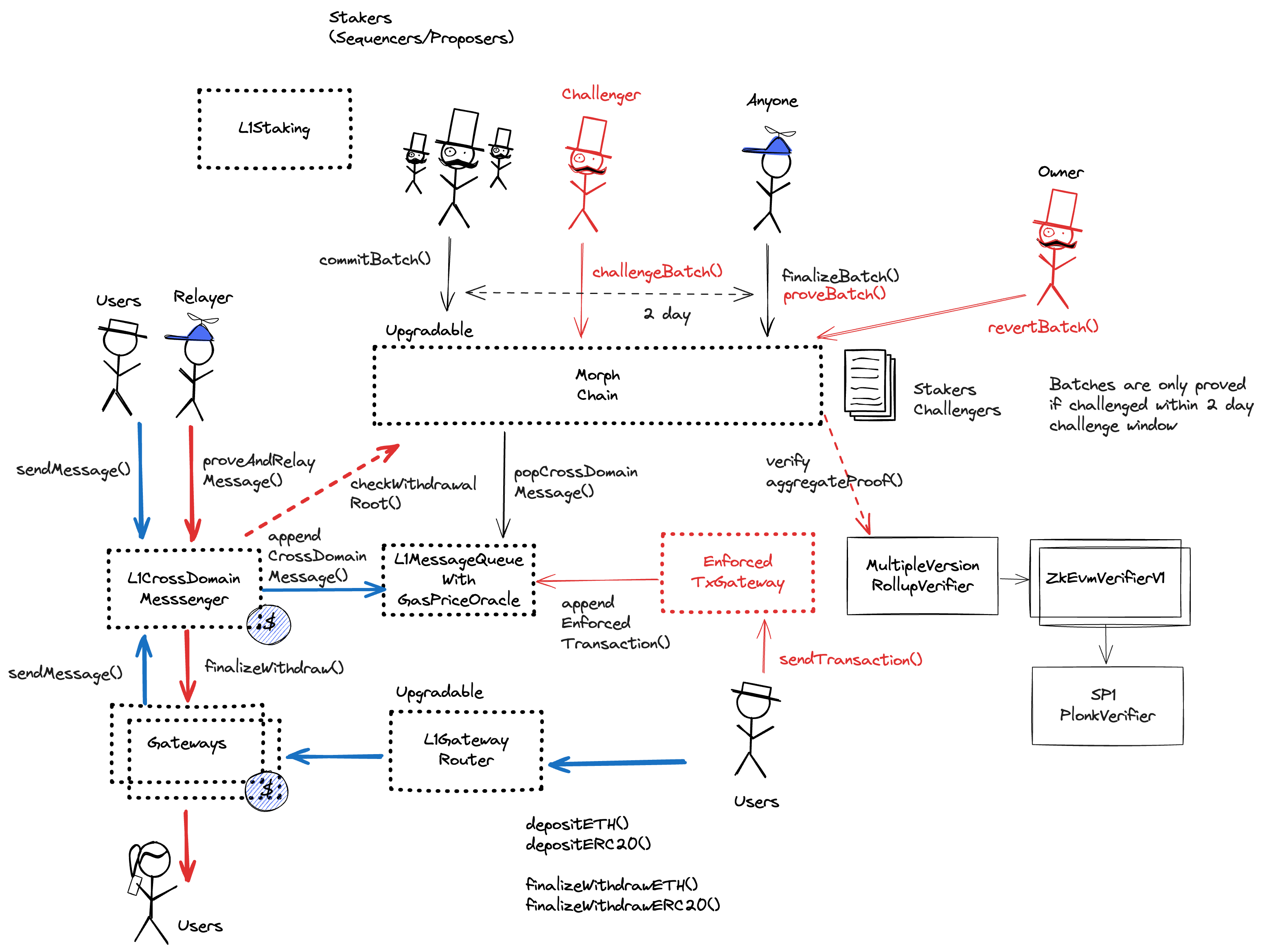
Fraud proofs allow actors watching the chain to prove that the state is incorrect. Single round proofs (1R) only require a single transaction to resolve. ZK proofs are used to prove the correctness of the state transition. The system currently operates with at least 5 whitelisted challengers external to the team.
All of the data needed for proof construction is published on Ethereum L1.
There is no window for users to exit in case of an unwanted regular upgrade since contracts are instantly upgradable.
Only the whitelisted proposers can publish state roots on L1, so in the event of failure the withdrawals are frozen.
All data required for proofs is published on chain
All the data that is used to construct the system state is published on chain in the form of cheap blobs or calldata. This ensures that it will be available for enough time.
Morph uses a one round fault proof system where whitelisted Challengers, if they find a faulty state root within the 2d challenge window, can post a 1 WEI bond and request a ZK proof of the state transition. At least 5 Challengers are operated by entities external to the team. After the challenge, during a 3d proving window, a ZK proof must be delivered, otherwise the state root is considered invalid and the root proposer bond, which is currently set to 1 ETH, is slashed. The zkVM used is SP1 from Succinct. If the valid proof is delivered, the Challenger loses the challenge bond. The Morph Multisig can revert unfinalized batches.
Funds can be stolen if no whitelisted challenger posts a challenge for an incorrect state root.
Program Hashes
Name | Hash | Repository | Verification | Used in | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
0x00ad...e13d | None | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
0x0059...8d7e | Code unknown | None | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Morph uses decentralised sequencer network
The system uses a decentralised sequencer/proposer network. At the moment all sequencers are run by Morph and - from the point of Ethereum - they don’t need to reach consensus on a block as any one of them can propose a block with an L2 state root on Ethereum. There is a plan to use tendermint with BLS signatures to verify consensus after Petra upgrade.
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can't force any transaction
There is no general mechanism to force the sequencer to include the transaction.
Users can be censored if the operator refuses to include their transactions.

Ethereum
Roles:
Allowed to challenge or delete state roots proposed by a Proposer.
Actors:
A Multisig with 3/5 threshold.
- Can interact with L1Staking
- Can interact with TimelockController
- cancel queued transactions
- propose transactions
- Can interact with MultipleVersionRollupVerifier
- register new verifiers to be used starting from a given L2 batch index
- Can interact with L1GatewayRouter
- manage token to escrow mapping and (un-)register escrows
- Can interact with Rollup
- can pause and unpause, revert unfinalized batches, update proof window and finalization period, manage challengers, modify the verifier address
- Can interact with EnforcedTxGateway
- pause and unpause, update the fee vault
- Can interact with Whitelist
- manage the whitelist
- A Challenger - acting directly
A Multisig with 4/6 threshold.
- Can upgrade with no delay
- L1Staking TimelockController → ProxyAdmin
- L1ETHGateway TimelockController → ProxyAdmin
- L1MessageQueueWithGasPriceOracle TimelockController → ProxyAdmin
- L1StandardERC20Gateway TimelockController → ProxyAdmin
- TimelockController ProxyAdmin
- L1GatewayRouter TimelockController → ProxyAdmin
- Rollup TimelockController → ProxyAdmin
- EnforcedTxGateway TimelockController → ProxyAdmin
- L1CrossDomainMessenger TimelockController → ProxyAdmin
- Can interact with TimelockController
- execute transactions that are ready
- manage all access control roles TimelockController - or - acting directly
- A Challenger - acting directly
- A Sequencer - acting directly

Ethereum
- Roles:
- owner: TimelockController
A timelock with access control. The current minimum delay is 0s.
- Roles:
- admin: ProxyAdmin; ultimately Morph Multisig 1
- canceller: Morph Multisig 2
- defaultAdmin: Morph Multisig 1, TimelockController; ultimately Morph Multisig 1
- executor: Morph Multisig 1
- proposer: Morph Multisig 2
Main entrypoint for depositing ETH and ERC20 tokens, which are then forwarded to the correct escrow.
- Roles:
- admin: ProxyAdmin; ultimately Morph Multisig 1
- owner: Morph Multisig 2
The main contract of the Morph rollup. Allows to post transaction data and state roots and implements the challenge mechanism along with the proof system. Sequencing and proposing are behind a whitelist. Although the contract exposes the external function commitBatchWithProof(), it currently reverts for non-whitelisted actors.
- Roles:
- admin: ProxyAdmin; ultimately Morph Multisig 1
- challengers: EOA 1, EOA 10, EOA 11, EOA 13, EOA 14, EOA 15, EOA 16, EOA 18, EOA 19, EOA 2, EOA 20, EOA 21, EOA 22, EOA 23, EOA 24, EOA 25, EOA 26, EOA 27, EOA 28, EOA 3, EOA 30, EOA 31, EOA 32, EOA 33, EOA 34, EOA 35, EOA 36, EOA 37, EOA 38, EOA 4, EOA 40, EOA 41, EOA 42, EOA 5, EOA 6, EOA 8, EOA 9, Morph Multisig 2
- owner: Morph Multisig 2
- Roles:
- owner: Morph Multisig 1
Contract used to send L1 -> L2 and relay messages from L2. It allows to replay failed messages and to drop skipped messages. L1 -> L2 messages sent using this contract pay for L2 gas on L1 and will have the aliased address of this contract as the sender.
- Roles:
- admin: ProxyAdmin; ultimately Morph Multisig 1
- This contract stores the following tokens: ETH.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
Program Hashes
Name | Hash | Repository | Verification | Used in | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
0x00ad...e13d | None | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
0x0059...8d7e | Code unknown | None | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
