Search
Search for projects by name or address
 Taiko Alethia
Taiko Alethia
Badges
About
Taiko Alethia is an Ethereum-equivalent rollup on the Ethereum network. Taiko aims at combining based sequencing and a multi-proof system through SP1, RISC0 and TEEs.
Badges
About
Taiko Alethia is an Ethereum-equivalent rollup on the Ethereum network. Taiko aims at combining based sequencing and a multi-proof system through SP1, RISC0 and TEEs.
Why is the project listed in others?
Consequence: projects without a proper proof system fully rely on single entities to safely update the state. A malicious proposer can finalize an invalid state, which can cause loss of funds.
Learn more about the recategorisation here.
2025 Mar 06 — 2026 Mar 06
The section shows the operating costs that L2s pay to Ethereum.
2025 Mar 06 — 2026 Mar 06
This section shows how much data the project publishes to its data-availability (DA) layer over time. The project currently posts data to![]() Ethereum.
Ethereum.
2025 Mar 06 — 2026 Mar 06
This section shows how "live" the project's operators are by displaying how frequently they submit transactions of the selected type. It also highlights anomalies - significant deviations from their typical schedule.
Preconfs introduction
2025 Aug 11th
Taiko implements preconfs - whitelisted actors provide fast soft confirmations for L2 txs.
Plonky3 vulnerability patch
2025 Jun 4th
SP1 verifier is patched to fix critical vulnerability in Plonky3 proof system (SP1 dependency).
Funds can be stolen if
Users can be censored if
MEV can be extracted if
Users can submit transactions to an L1 queue, but can’t force them. The sequencers cannot selectively skip transactions but can stop processing the queue entirely. In other words, if the sequencers censor or are down, they are so for everyone.
A multi-proof system is used. There are four verifiers available: SGX (Geth), SGX (Reth), SP1 and RISC0. Two of them must be used to prove a block, and SGX (Geth) is mandatory. A block can be proved without providing a ZK proof as SGX (Geth) + SGX (Reth) is a valid combination.
All of the data needed for proof construction is published on Ethereum L1.
There is no window for users to exit in case of an unwanted upgrade since contracts are instantly upgradable.
Anyone can be a Proposer and propose new roots to the L1 bridge. Proofs can only be submitted for blocks sequenced by whitelisted operators. Provers are required to submit two valid proofs for blocks, one of which must be SGX (Geth), and the other can be either SGX (Reth), SP1, or RISC0. If the initial proposer fails to prove the block within the proving window, they forfeit half of their liveness bond.
All data required for proofs is published on chain
All the data that is used to construct the system state is published on chain in the form of blobs. This ensures that it will be available for enough time.
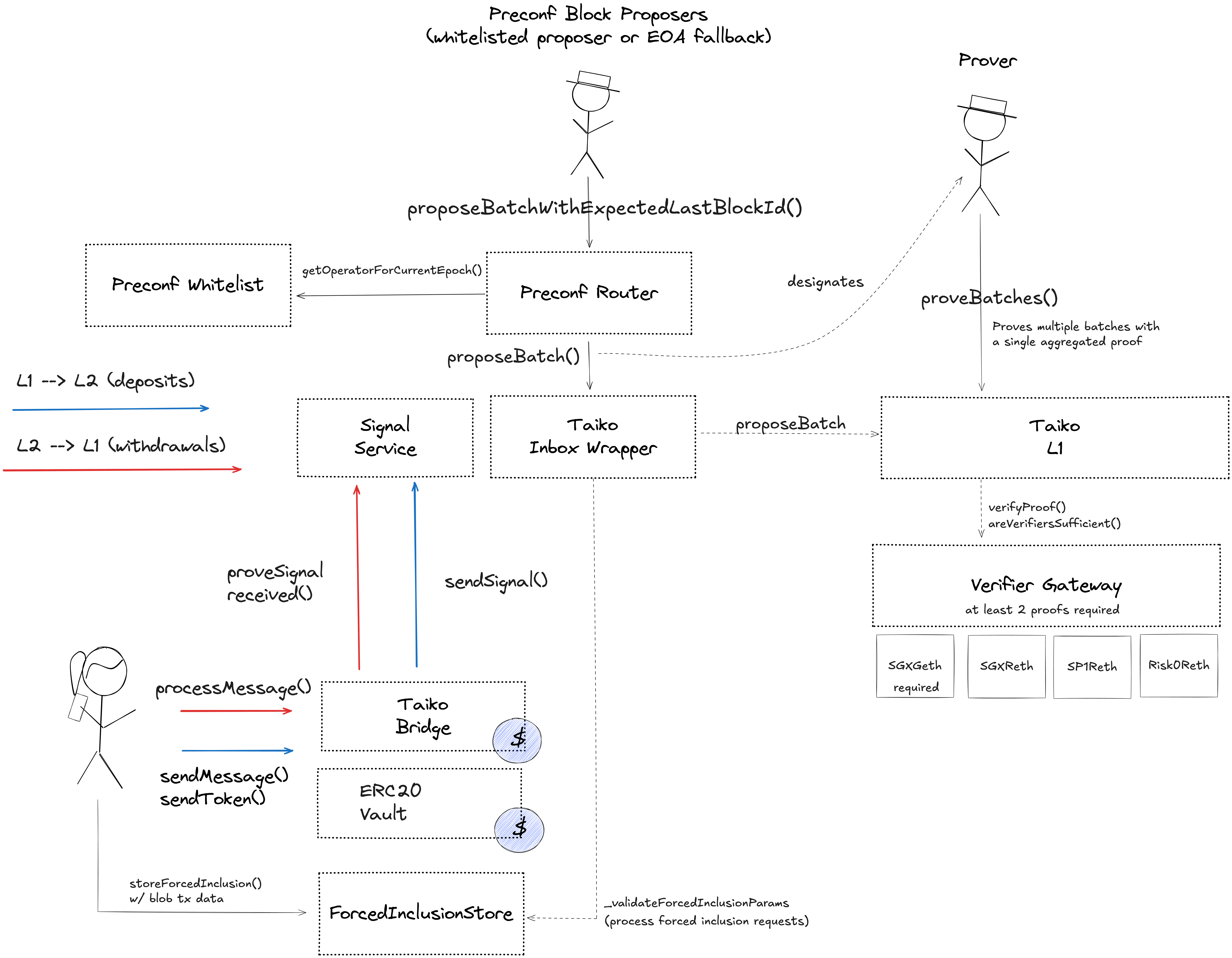
Taiko uses a multi-proof system to validate state transitions. The system requires two proofs among four available verifiers: SGX (Geth), SGX (Reth), SP1, and RISC0. The use of SGX (Geth) is mandatory, while the other three can be used interchangeably. This means that a block can be proven without providing a ZK proof if SGX (Geth) and SGX (Reth) are used together. Batch proposers are required to stake a liveness bond of 25.0 TAIKO, half of which is forfeited if they fail to prove the block within the proving window of 2h. The multi-proof system allows to detect bugs in the verifiers if they produce different results for the same block. If such a bug is detected, the system gets automatically paused.
Funds can be stolen if a malicious block is proven by compromised SGX instances.
The system uses whitelist-based rotating operators
The system uses a whitelist-based sequencing mechanism to allow for fast preconfirmations on the L2. On the L1, whitelisted preconfirmers (or the fallback operator) can sequence Taiko L2 blocks by proposing them on the TaikoL1 contract.
The whitelist is managed by the PreconfWhitelist contract, which currently has 3 active operators registered.
The proposer of a block is assigned the designated prover role, and will be the only entity allowed to provide a proof for the block during the 2h proving window.
Currently, proving a block requires the block proposer to run a SGX instance with Geth, plus either SGX (Reth), SP1, or RISC0 to prove the block.
Unless the block proposer proves the block within the proving window, it will forfeit half of its liveness bond to the TaikoL1 smart contract.
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force any transaction via L1
Users can submit a blob containing a standalone transaction by calling the storeForcedInclusion() function on the ForcedInclusionStore contract.
This forced transaction mechanism allows users to submit a transaction without running a prover.
This mechanism ensures that at least one forced transaction from the queue is processed every 255 batches. However, if many transactions (k) are added to the queue, an individual transaction could experience a worst-case delay of up to k * 255 batches while waiting for its turn. Also, right now there is no mechanism that forces L2 Sequencer to include transactions from the queue in an L2 block, since L1 batches submission is permissioned behind a whitelist.
Users can be censored if the operator refuses to include their transactions.

Ethereum
Roles:
Actors:
The main contract and entrypoint of the Aragon-based DAO governance framework. Fine-grained DAO permissions, proposals, voting and thresholds are configured here.
- Can upgrade with no delay
- ForcedInclusionStore TaikoDAOController
- TaikoL1 TaikoDAOController
- AutomataDcapV3Attestation TaikoDAOController
- Taiko Token TaikoDAOController
- DefaultResolver TaikoDAOController
- Risc0VerifierGateway TaikoDAOController
- TaikoDAOController
- SgxVerifier TaikoDAOController
- AutomataDcapV3Attestation TaikoDAOController
- DefaultResolver TaikoDAOController
- QuotaManager TaikoDAOController
- MainnetERC20Vault TaikoDAOController
- MainnetSignalService TaikoDAOController
- SgxVerifier TaikoDAOController
- TaikoWrapper TaikoDAOController
- VerifierGateway TaikoDAOController
- SP1VerifierGateway TaikoDAOController
- PreconfRouter TaikoDAOController
- MainnetBridge TaikoDAOController
- L1SharedAddressManager TaikoDAOController
- TaikoDAOController
- PreconfWhitelist TaikoDAOController
- Can interact with AutomataDcapV3Attestation
- can update the program being verified TaikoDAOController
- Can interact with DefaultResolver
- can update the contract address for a given name TaikoDAOController
- Can interact with Risc0VerifierGateway
- can update the program being verified TaikoDAOController
- Can interact with SgxVerifier
- can add new instances without a DCAP attestation TaikoDAOController
- Can interact with AutomataDcapV3Attestation
- can update the program being verified TaikoDAOController
- Can interact with DefaultResolver
- can update the contract address for a given name TaikoDAOController
- Can interact with SgxVerifier
- can add new instances without a DCAP attestation TaikoDAOController
- Can interact with SP1VerifierGateway
- can update the program being verified TaikoDAOController
- Can interact with L1SharedAddressManager
- can update the contract address for a given name TaikoDAOController
A Multisig with 2/3 threshold.
A Multisig with 4/6 threshold.
- A Sequencer - acting directly
Member of Taiko Foundation Treasury Multisig, Taiko Multisig.
- Can upgrade with no delay
- ProverSet
Taiko Alethia
Actors:
- Can upgrade with no delay
- Bridge
- SignalService
- L2AddressManager
- TaikoAnchor
- DefaultResolver
- DelegateController
- Can interact with L2AddressManager
- can update the contract address for a given name
- Can interact with DefaultResolver
- can update the contract address for a given name

Ethereum
Shared vault for Taiko chains for bridged ERC20 tokens.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- This contract can store any token.
Middleware contract that maintains ownership of DAO-controlled assets and contracts. Its token weight does not count towards the DAO quorum. Member of Taiko Foundation Treasury Multisig.
- Roles:
- admin: DAO
- owner: DAO
Middleware contract that maintains ownership of DAO-controlled assets and contracts. Its token weight does not count towards the DAO quorum.
- Roles:
- admin: DAO
- owner: DAO
Contract that allows users to enqueue forced transactions via L1. The system guarantees that at least one pending forced transaction from the queue will be processed every 255 batches. Individual transactions may face longer delays if the queue is extensive.
- Roles:
- admin: TaikoDAOController; ultimately DAO
A signer list for registering agents, similar to a Multisig.
Contract managing SGX attestation certificates.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
ERC20 contract implementing the TAIKO token. It defines a list of addresses designated as non-voting.
- Roles:
- admin: TaikoDAOController; ultimately DAO
Modular Governance contract allowing for proposing, voting on and executing encrypted proposals (e.g. for Security Council emergency proposals).
A registry for signers (of the Security Council) to appoint agents to operate on their behalf. These agents can also register their encryption keys for encrypted emergency proposal support.
Maps contract names to contract addresses. Changes in this mapping effectively act as contract upgrades.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
Entry contract to verify batches using RISC Zero.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
Contract managing SGX attestation certificates.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
Maps contract names to contract addresses. Changes in this mapping effectively act as contract upgrades.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
Defines withdrawal limits per token.
- Roles:
- admin: TaikoDAOController; ultimately DAO
An optimistic governance module. Proposals pass and can be executed unless 10% of votable TAIKO veto them within 7d.
Entry point for proposing blocks. It enforces the inclusion of forced transactions after their deadline.
- Roles:
- admin: TaikoDAOController; ultimately DAO
Gateway contract for the multi-proof system. It redirects proof to the appropriate verifier based on the proof type.
- Roles:
- admin: TaikoDAOController; ultimately DAO
Entry contract to verify batches using SP1.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
Entry point for batch proposals under the pre-confirmation architecture. It allows batches to be proposed only by whitelisted addresses.
- Roles:
- admin: TaikoDAOController; ultimately DAO
Shared bridge for Taiko chains for bridged ETH.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- This contract stores the following tokens: ETH.
Modular Governance contract allowing for proposing, voting on and executing proposals (e.g. for Security Council standard proposals).
Maps contract names to contract addresses. Changes in this mapping effectively act as contract upgrades.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- owner: TaikoDAOController; ultimately DAO
Contains the whitelist of addresses allowed to propose batches on L1. These operators can also issue pre-confirmation from their public addresses. Currently, there are 3 operators registered.
- Roles:
- admin: TaikoDAOController; ultimately DAO
- getOperatorCandidatesForCurrentEpoch: EOA 1, EOA 3, EOA 4
Verifier contract for SP1 proofs (v5.0.0).
Taiko Alethia
- Roles:
- admin: DelegateController
- Roles:
- admin: DelegateController
Maps contract names to contract addresses. Changes in this mapping effectively act as contract upgrades.
- Roles:
- admin: DelegateController
- owner: DelegateController
Maps contract names to contract addresses. Changes in this mapping effectively act as contract upgrades.
- Roles:
- admin: DelegateController
- owner: DelegateController
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
