Search
Search for projects by name or address
 Zircuit
Zircuit
Badges
About
Zircuit is a universal ZK Rollup. It is based on the Optimism Bedrock architecture, employing AI to identify and stop malicious transactions at the sequencer level.
Badges
About
Zircuit is a universal ZK Rollup. It is based on the Optimism Bedrock architecture, employing AI to identify and stop malicious transactions at the sequencer level.
2025 Feb 17 — 2026 Feb 17
The section shows the operating costs that L2s pay to Ethereum.
2025 Feb 17 — 2026 Feb 17
This section shows how much data the project publishes to its data-availability (DA) layer over time. The project currently posts data to![]() Ethereum.
Ethereum.
2025 Feb 17 — 2026 Feb 17
This section shows how "live" the project's operators are by displaying how frequently they submit transactions of the selected type. It also highlights anomalies - significant deviations from their typical schedule.
Proof system migrated to SP1
2025 Aug 25th
Zircuit deprecates its in-house proof system in favor of SP1.
Funds can be stolen if
Funds can be frozen if
Users can be censored if
MEV can be extracted if
STARKs and SNARKs are zero knowledge proofs that ensure state correctness. STARKs proofs are wrapped in SNARKs proofs for efficiency. SNARKs require a trusted setup.
All of the data needed for proof construction is published on Ethereum L1.
There is no window for users to exit in case of an unwanted regular upgrade since contracts are instantly upgradable.
Users are able to trustlessly exit by submitting a Merkle proof of funds after 1mo with no new state proposals have passed. The escape of ETH and ERC-20 balances is permissionless while the escape of DeFi contract balances is trusted.
All data required for proofs is published on chain
All the data that is used to construct the system state is published on chain in the form of cheap blobs or calldata. This ensures that it will be available for enough time.
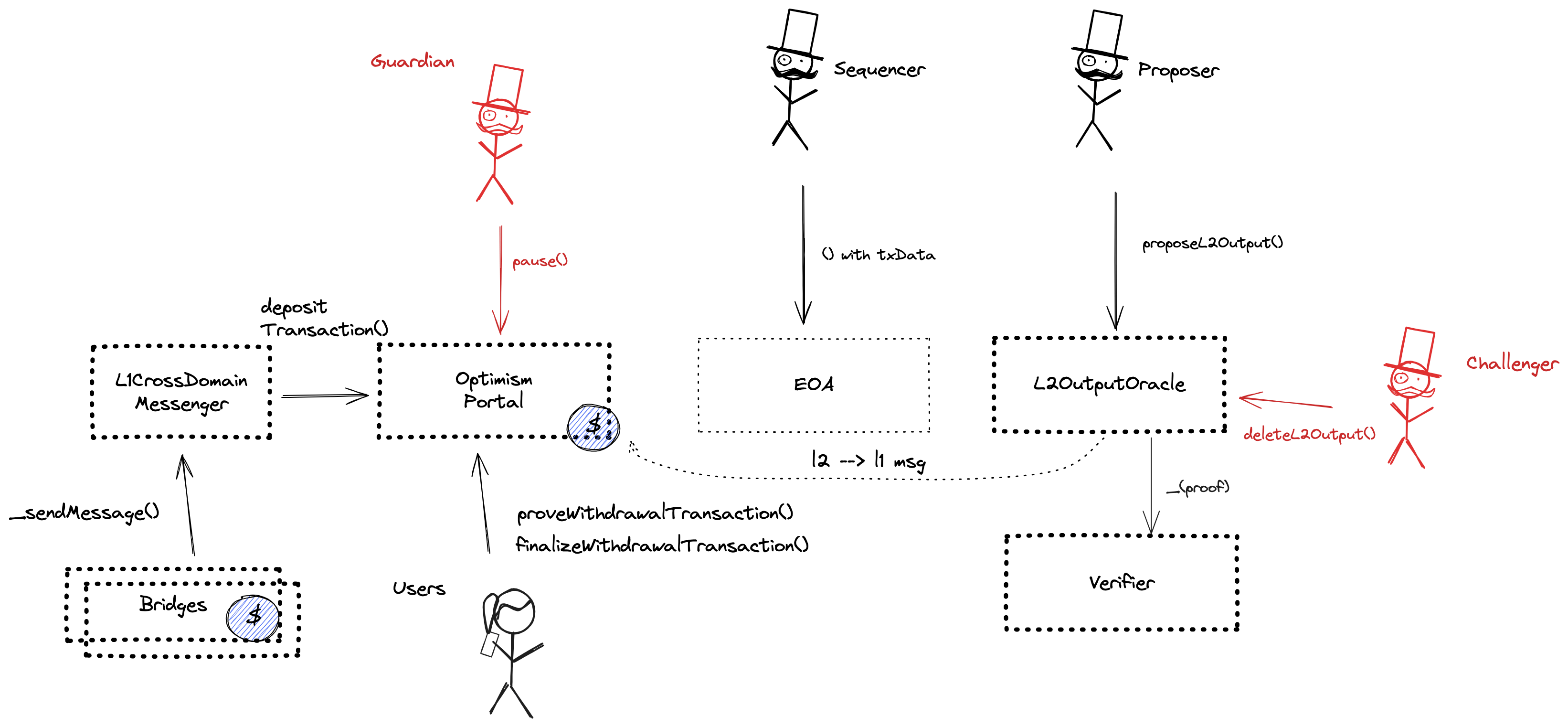
- Derivation: Batch submission - OP Mainnet specs
- BatchInbox - address
- OptimismPortal.sol - source code, depositTransaction function
Each update to the system state must be accompanied by a ZK proof that ensures that the new state was derived by correctly applying a series of valid user transactions to the previous state. These proofs are then verified on Ethereum by a smart contract.
Funds can be stolen if the validity proof cryptography is broken or implemented incorrectly.
Funds can be frozen if the SP1VerifierGateway is unable to route proof verification to a valid verifier.
The system has a centralized operator
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force any transaction
Because the state of the system is based on transactions submitted on the underlying host chain and anyone can submit their transactions there it allows the users to circumvent censorship by interacting with the smart contract on the host chain directly.
Regular messaging
Funds can be frozen if the centralized validator goes down. Users cannot produce blocks themselves and exiting the system requires new block production (CRITICAL).
Forced messaging
If the user experiences censorship from the operator with regular L2->L1 messaging they can submit their messages directly on L1. The system is then obliged to service this request or halt all messages, including forced withdrawals from L1 and regular messages initiated on L2. Once the force operation is submitted and if the request is serviced, the operation follows the flow of a regular message.
Users can be censored if the operator explicitly censors their forced transaction, possible through a modification in the smart contracts.
Escape mechanism
Zircuit employs a custom escape mechanism that can help users exit the system in certain situations. If the operator disappears or is down for more than 1mo, users can submit a merkle proof to the L1 contracts to withdraw any ETH or ERC-20 balance they have on L2. L2 DeFi contracts and their deployers can manually distribute their pooled L2 balance using ‘Resolver’ contracts on L1 in case of an escape. In contrast to individual account escapes, the redistribution of these contract balances to users is permissioned.
EVM compatible smart contracts are supported
OP stack chains are pursuing the EVM Equivalence model. No changes to smart contracts are required regardless of the language they are written in, i.e. anything deployed on L1 can be deployed on L2.

Ethereum
Roles:
Allowed to challenge or delete state roots proposed by a Proposer.
Allowed to pause withdrawals. In op stack systems with a proof system, the Guardian can also blacklist dispute games and set the respected game type (permissioned / permissionless).
Allowed to post new state roots of the current layer to the host chain.
Allowed to commit transactions from the current layer to the host chain.
Actors:
A Multisig with 4/6 threshold.
- Can upgrade with no delay
- OptimismPortal ProxyAdmin
- L1CrossDomainMessenger ProxyAdmin
- SystemConfig ProxyAdmin
- L1StandardBridge ProxyAdmin
- ResolverRegistry ProxyAdmin
- ZircuitSuperchainConfig ProxyAdmin
- L2OutputOracle ProxyAdmin
- L1ERC721Bridge ProxyAdmin
- OptimismMintableERC20Factory ProxyAdmin
- Can interact with SystemConfig
- Can interact with SP1VerifierGateway
- A Challenger - acting directly
A Multisig with 2/5 threshold.
- Can interact with ZircuitSuperchainConfig
- manage roles including the guardian role
- A Guardian - acting directly
- A Sequencer - acting directly
- A Proposer - acting directly
Zircuit
Actors:
A Multisig with 4/6 threshold.
- Can upgrade with no delay
- L1Block ProxyAdmin
- ProxyAdmin ProxyAdmin

Ethereum
The main entry point to deposit funds from the host chain to this chain. It also allows to prove and finalize withdrawals. This fork of the standard OP stack contract allows for permissionless ‘escaping’ of assets with merkle proofs or a resolver if there were no state updates for a time defined by the L2OutputOracle.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
- guardian: Zircuit Multisig 2
- This contract stores the following tokens: ETH.
Entrypoint for permissioned proposers to propose new L2 outputs (state roots). New proposals have to be accompanied by a zk-SNARK proof of a correct state transition. Users can ‘escape’ their funds after 1mo of no state updates by supplying merkle proofs or using a resolver.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
- challenger: Zircuit Multisig 1
- proposer: EOA 2
This is NOT the shared SuperchainConfig contract of the OP stack Superchain but rather a local fork. It manages the PAUSED_SLOT, a boolean value indicating whether the local chain is paused, and access control for configuring actors who can pause and unpause the system.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
- defaultAdmin: Zircuit Multisig 2
Sends messages from host chain to this chain, and relays messages back onto host chain. In the event that a message sent from host chain to this chain is rejected for exceeding this chain’s epoch gas limit, it can be resubmitted via this contract’s replay function.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
The main entry point to deposit ERC20 tokens from the host chain to this chain. This fork of the standard OP stack contract allows for permissionless ‘escaping’ of assets with merkle proofs or a resolver if there were no state updates for a configurable time.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
- This contract can store any token.
Used to bridge ERC-721 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
- Roles:
- owner: Zircuit Multisig 1
Registers ‘resolvers’ which are allowed to supply authoritative data for blockchain balances to support escapes without merkle proofs from e.g. DeFi smart contracts on L2. A resolver can either be registered directly by the respective contract on L2 or by its deployer from L1, using deterministic deployment derivation.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
Escrow for custom external tokens that use the canonical bridge for messaging but are governed externally.
- This contract stores the following tokens: wstETH.
A helper contract that generates OptimismMintableERC20 contracts on the network it’s deployed to. OptimismMintableERC20 is a standard extension of the base ERC20 token contract designed to allow the L1StandardBridge contracts to mint and burn tokens. This makes it possible to use an OptimismMintableERC20 as this chain’s representation of a token on the host chain, or vice-versa.
- Roles:
- admin: ProxyAdmin; ultimately Zircuit Multisig 1
Zircuit
- Roles:
- admin: ProxyAdmin; ultimately GnosisSafe
- owner: GnosisSafe
Value Secured is calculated based on these smart contracts and tokens:
Main entry point for users depositing ERC20 token that do not require custom gateway.
custom wstETH Vault controlled by Lido governance, using the canonical bridge for messaging.
Main entry point for users depositing ETH.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
