L2BEAT Bridges is a work in progress. You might find incomplete research or inconsistent naming. Join our Discord to suggest improvements!
 Immutable zkEVM
Immutable zkEVM
About
Immutable zkEVM is a sidechain focused on gaming and powered by Polygon stack. It plans to eventually transition to a ZK Rollup.
About
Immutable zkEVM is a sidechain focused on gaming and powered by Polygon stack. It plans to eventually transition to a ZK Rollup.
Funds can be stolen if
- validators decide to mint more tokens than there are locked on Ethereum thus preventing some existing holders from being able to bring their funds back to Ethereum,
- validators relay a withdraw request that wasn't originated on the source chain,
- a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
Users can be censored if
Principle of Operation
Immutable zkEVM bridge makes use of Axelar network to transfer assets between Ethereum and Immutable zkEVM. A deposit starts by a user depositing tokens on the Bridge contract and then the tokens are minted on the destination chain.
Withdrawals to Ethereum can be delayed by a predefined time with a flow rate mechanism that controls outflows of the bridge escrow. The ProxyAdmin or an address with the rate_control role can define so-called buckets for each token: Each bucket has a capacity and a refill rate. All withdrawals that exceed the tokens bucket capacity trigger the withdrawal queue, which delays subsequent withdrawals of any of the bridges’ assets for a time defined in withdrawalDelay (currently 1d).
Validators running PoS consensus
Messages are verified by the Validators running the Axelar network which, technically, is a Cosmos chain. As in any standard Cosmos chain, Validators are bonded by staking tokens and can be slashed for misbehavior.
Users can be censored if validators on Axelar decide to not mint tokens after observing an event on Ethereum.
Funds can be stolen if validators decide to mint more tokens than there are locked on Ethereum thus preventing some existing holders from being able to bring their funds back to Ethereum.
Funds can be stolen if validators relay a withdraw request that wasn't originated on the source chain.
Destination tokens are not upgradable
Tokens on the destination end up as wrapped ERC20 proxies that are not upgradable, using EIP-1167.
The system uses the following set of permissioned addresses:
This is a Gnosis Safe with 4 / 6 threshold. Multisig controlling the ProxyAdmin, potentially stealing all locked funds.
Those are the participants of the OwnerMultisig.
Contract allowed to upgrade the Bridge, its flow rate control and the Axelar adaptor.
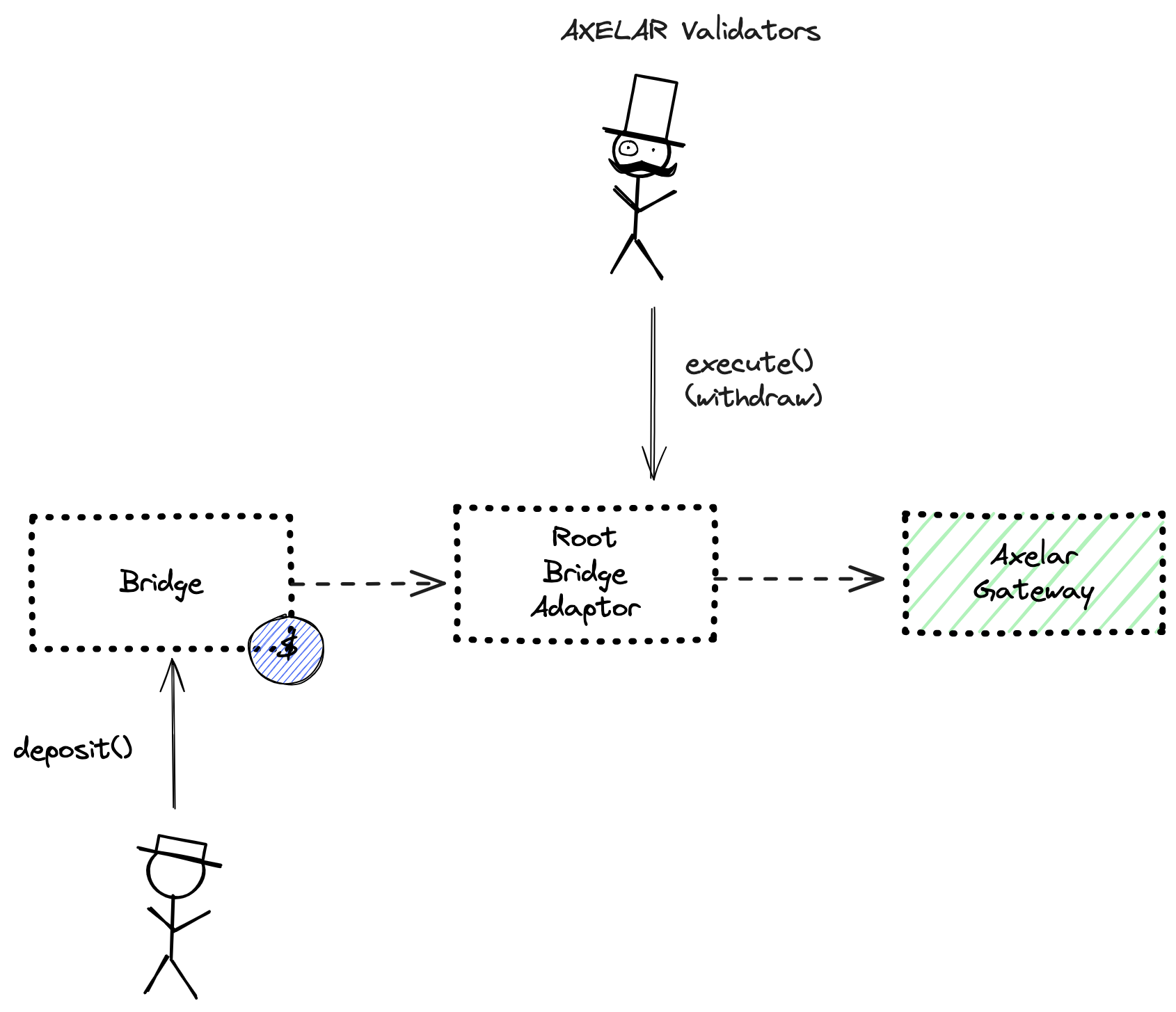
The system consists of the following smart contracts on the host chain (Ethereum):
Main escrow for tokens. This contract stores the following tokens: IMX, USDC, ETH, USDT, GOG.
Upgrade delay: No delay
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).