Search
Search for projects by name or address
 Automata
Automata
Badges
About
Automata Network is an OP stack based Layer 2 Optimium acting as a modular attestation layer that extends machine-level trust to Ethereum with TEE Coprocessors and an EigenLayer AVS.
Badges
About
Automata Network is an OP stack based Layer 2 Optimium acting as a modular attestation layer that extends machine-level trust to Ethereum with TEE Coprocessors and an EigenLayer AVS.
Why is the project listed in others?
Consequence: projects without a proper proof system fully rely on single entities to safely update the state. A malicious proposer can finalize an invalid state, which can cause loss of funds.
Consequence: projects without a data availability bridge fully rely on single entities (the sequencer) to honestly rely available data roots on Ethereum. A malicious sequencer can collude with the proposer to finalize an unavailable state, which can cause loss of funds.
Learn more about the recategorisation here.
2025 Feb 28 — 2026 Feb 28
The section shows the operating costs that L2s pay to Ethereum.
2025 Feb 28 — 2026 Feb 28
This section shows how "live" the project's operators are by displaying how frequently they submit transactions of the selected type. It also highlights anomalies - significant deviations from their typical schedule.
Funds can be stolen if
- the sequencer is malicious and is able to economically outspend the altruistic challengers,
- there is no challenger willing to challenge unavailable data commitments,
- a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL),
- an invalid state root is submitted to the system (CRITICAL).
Funds can be frozen if
MEV can be extracted if
Currently the system permits invalid state roots. More details in project overview.
Proof construction and state derivation rely fully on data that is NOT published onchain. A custom data availability (DA) provider without attestations is used, but data unavailability can be challenged.
There is no window for users to exit in case of an unwanted regular upgrade since contracts are instantly upgradable.
Only the whitelisted proposers can publish state roots on L1, so in the event of failure the withdrawals are frozen.
Automata DA is a data availability solution using data availability challenges (DA Challenges).
There are no onchain assets at risk of being slashed in case of a data withholding attack. However, there is a mechanism that allows users to challenge unavailability of data. The system is not secure if the malicious sequencer is able to outspend the altruistic challengers, and there is no pool of funds onchain to incentivize challengers.
There is no fraud detection mechanism in place. A data withholding attack can only be detected by nodes downloading the full data from the DA layer.
The committee does not meet basic security standards, either due to insufficient size, lack of member diversity, or poorly defined threshold parameters. The system lacks an effective DA bridge and it is reliant on the assumption of an honest sequencer, creating significant risks to data integrity and availability.
There is no delay in the upgradeability of the bridge. Users have no time to exit the system before the bridge implementation update is completed.
The relayer role is permissioned, and the DA bridge does not have a Security Council or a governance mechanism to propose new relayers. In case of relayer failure, the DA bridge will halt and be unable to recover without the intervention of a centralized entity.
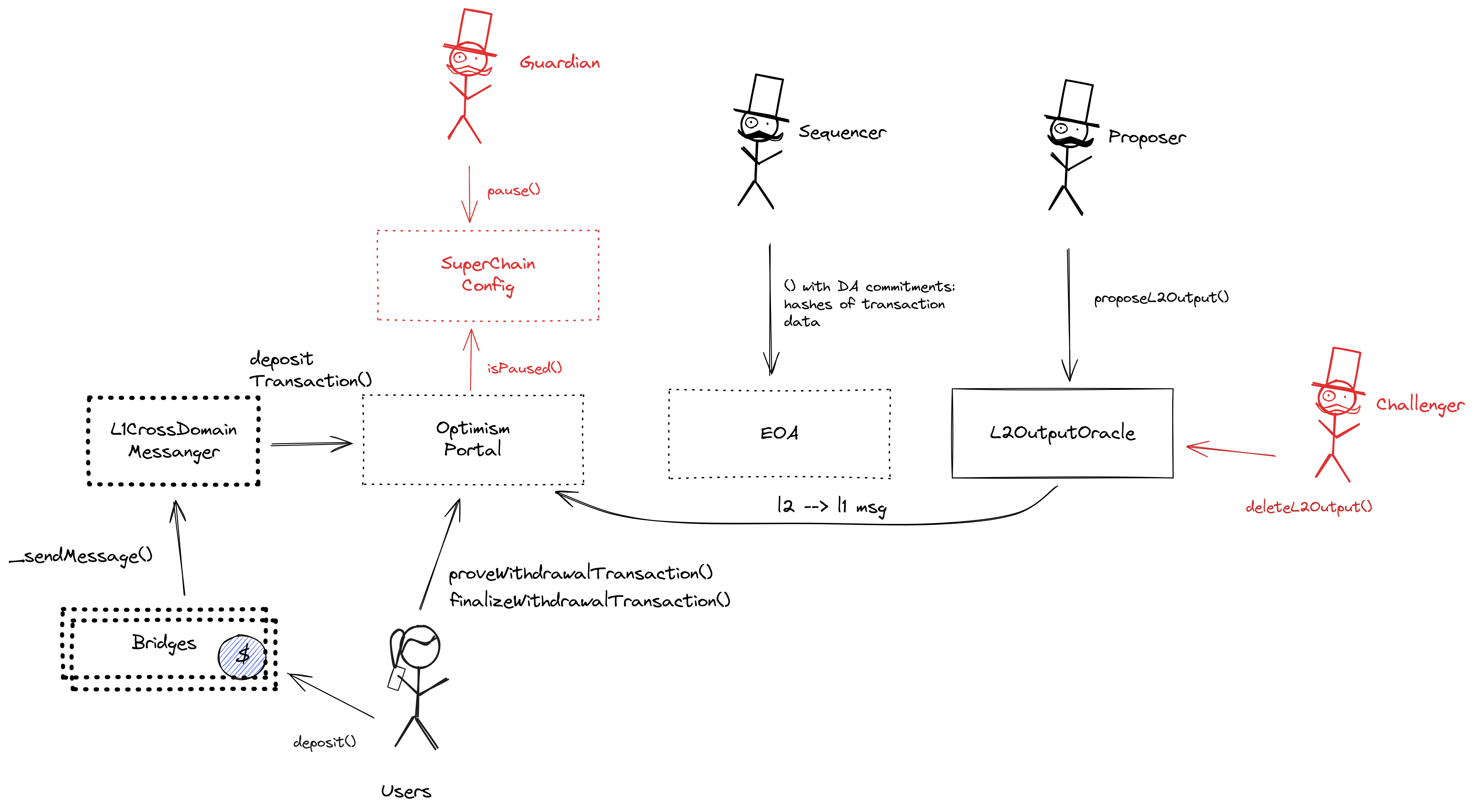
Architecture

Data Availability Challenges
Automata relies on DA challenges for data availability. The DA Provider submits an input commitment on Ethereum, and users can request the data behind the commitment off-chain from the DA Provider. If a DA challenger finds that the data behind a tx data commitment is not available, they can submit a challenge which requires locking a bond within 12h. A challenge can be resolved by publishing the preimage data within an additional 12h. In such case, a portion of the challenger bond is burned, with the exact amount estimated as the cost incurred by the resolver to publish the full data, meaning that the resolver and challenger will approximately lose the same amount of funds. The system is not secure if the malicious sequencer is able to outspend the altruistic challengers. If instead, after a challenge, the preimage data is not published, the chain reorgs to the last fully derivable state.
DA Bridge
Only hashes of data batches are posted as DA commitments to an EOA on Ethereum. However, there is a mechanism that allows users to challenge unavailability of data.
Funds can be lost if the sequencer posts an invalid data availability certificate and there are no challengers.
Funds can be lost if the sequencer posts an invalid data availability certificate, and he is able to outspend the challengers.
OP Stack projects can use the OP fault proof system, already being deployed on some. This project though is not using fault proofs yet and is relying on the honesty of the permissioned Proposer and Challengers to ensure state correctness. The smart contract system permits invalid state roots.
Funds can be stolen if an invalid state root is submitted to the system (CRITICAL).
The system has a centralized operator
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force any transaction
Because the state of the system is based on transactions submitted on the underlying host chain and anyone can submit their transactions there it allows the users to circumvent censorship by interacting with the smart contract on the host chain directly.
Regular messaging
Funds can be frozen if the centralized validator goes down. Users cannot produce blocks themselves and exiting the system requires new block production (CRITICAL).
Forced messaging
If the user experiences censorship from the operator with regular L2->L1 messaging they can submit their messages directly on L1. The system is then obliged to service this request or halt all messages, including forced withdrawals from L1 and regular messages initiated on L2. Once the force operation is submitted and if the request is serviced, the operation follows the flow of a regular message.
EVM compatible smart contracts are supported
OP stack chains are pursuing the EVM Equivalence model. No changes to smart contracts are required regardless of the language they are written in, i.e. anything deployed on L1 can be deployed on L2.

Ethereum
Roles:
Allowed to challenge or delete state roots proposed by a Proposer.
Allowed to pause withdrawals. In op stack systems with a proof system, the Guardian can also blacklist dispute games and set the respected game type (permissioned / permissionless).
Allowed to post new state roots of the current layer to the host chain.
Allowed to commit transactions from the current layer to the host chain.
Actors:
A Multisig with 3/4 threshold.
- Can upgrade with no delay
- L1ERC721Bridge ProxyAdmin
- DataAvailabilityChallenge ProxyAdmin
- SystemConfig ProxyAdmin
- L1CrossDomainMessenger ProxyAdmin
- OptimismMintableERC20Factory ProxyAdmin
- OptimismPortal ProxyAdmin
- L2OutputOracle ProxyAdmin
- SuperchainConfig ProxyAdmin
- L1StandardBridge ProxyAdmin
- Can interact with AddressManager
- set and change address mappings ProxyAdmin
- A Proposer - acting directly
- A Challenger - acting directly
- A Guardian - acting directly
- A Sequencer - acting directly
Member of Automata Multisig 2.
- Can interact with DataAvailabilityChallenge
- can upgrade the parameters of DA challenges like the bond size or refund percentages, potentially making challenges infeasable or insecure

Ethereum
The DataAvailabilityChallenge contract is used to challenge the full availability of data behind commimted transaction data hashes. See the technology section for more details.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
- owner: EOA 5
The main entry point to deposit funds from host chain to this chain. It also allows to prove and finalize withdrawals.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
- guardian: EOA 3
- This contract stores the following tokens: ETH, ATA.
Contains a list of proposed state roots which Proposers assert to be a result of block execution. Currently only the PROPOSER address can submit new state roots.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
- challenger: EOA 2
- proposer: EOA 1
This is NOT the shared SuperchainConfig contract of the OP stack Superchain but rather a local fork. It manages the PAUSED_SLOT, a boolean value indicating whether the local chain is paused, and GUARDIAN_SLOT, the address of the guardian which can pause and unpause the system.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
- guardian: EOA 3
Used to bridge ERC-721 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
Sends messages from host chain to this chain, and relays messages back onto host chain. In the event that a message sent from host chain to this chain is rejected for exceeding this chain’s epoch gas limit, it can be resubmitted via this contract’s replay function.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
The main entry point to deposit ERC20 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
- This contract can store any token.
- Roles:
- owner: Automata Multisig 1
A helper contract that generates OptimismMintableERC20 contracts on the network it’s deployed to. OptimismMintableERC20 is a standard extension of the base ERC20 token contract designed to allow the L1StandardBridge contracts to mint and burn tokens. This makes it possible to use an OptimismMintableERC20 as this chain’s representation of a token on the host chain, or vice-versa.
- Roles:
- admin: ProxyAdmin; ultimately Automata Multisig 1
Value Secured is calculated based on these smart contracts and tokens:
Main entry point for users depositing ERC20 token that do not require custom gateway.
Main entry point for users depositing ETH, ATA.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
