Search
Search for projects by name or address
 Kroma
Kroma
Kroma shut down on June 30, 2025. After this date, funds retrieval is not guaranteed. See announcement for details.
Badges
About
Kroma aims to develop a universal ZK Rollup based on the Optimism Bedrock architecture. Currently, Kroma operates as an Optimistic Rollup with ZK fault proofs, utilizing a zkEVM based on Scroll and a zkVM based proven with SP1.
Tokens breakdown
Badges
About
Kroma aims to develop a universal ZK Rollup based on the Optimism Bedrock architecture. Currently, Kroma operates as an Optimistic Rollup with ZK fault proofs, utilizing a zkEVM based on Scroll and a zkVM based proven with SP1.
Why is the project listed in others?
Consequence: projects without a proper proof system fully rely on single entities to safely update the state. A malicious proposer can finalize an invalid state, which can cause loss of funds.
Learn more about the recategorisation here.
2023 Sep 05 — 2026 Feb 24
The section shows the operating costs that L2s pay to Ethereum.
2023 Sep 05 — 2026 Feb 24
This section shows how much data the project publishes to its data-availability (DA) layer over time. The project currently posts data to![]() Ethereum.
Ethereum.
2024 Apr 25 — 2026 Feb 24
This section shows how "live" the project's operators are by displaying how frequently they submit transactions of the selected type. It also highlights anomalies - significant deviations from their typical schedule.
2023 Sep 05 — 2026 Feb 25
Kroma shutdown announcement
2025 Jun 20th
Kroma announces its shutdown on June 30, 2025. Users must withdraw their funds before that date.
Plonky3 vulnerability patch
2025 Jun 4th
SP1 verifier is patched to fix critical vulnerability in Plonky3 proof system (SP1 dependency).
Funds can be stolen if
Funds can be lost if
MEV can be extracted if
Fraud proofs allow actors watching the chain to prove that the state is incorrect. Interactive proofs (INT) require multiple transactions over time to resolve. ZK proofs are used to adjudicate the correctness of the last step. The challenge protocol can fail under certain conditions. The current system doesn’t use posted L2 txs batches on L1 as inputs to prove a fault (for the zkEVM prover path), meaning that DA is not always enforced.
All of the data needed for proof construction is published on Ethereum L1.
There is no window for users to exit in case of an unwanted regular upgrade since contracts are instantly upgradable.
Kroma nodes source code, including full node, proposer and validator, can be found here. Also, the geth server, source maintained here, is a fork of go-ethereum. For more details on how they are different from the Optimism implementation, see here. The instructions to run the proposer (called validator) and the ZK prover, are documented here.
Data batches are compressed using the zlib algorithm with best compression level.
The genesis file can be found here.
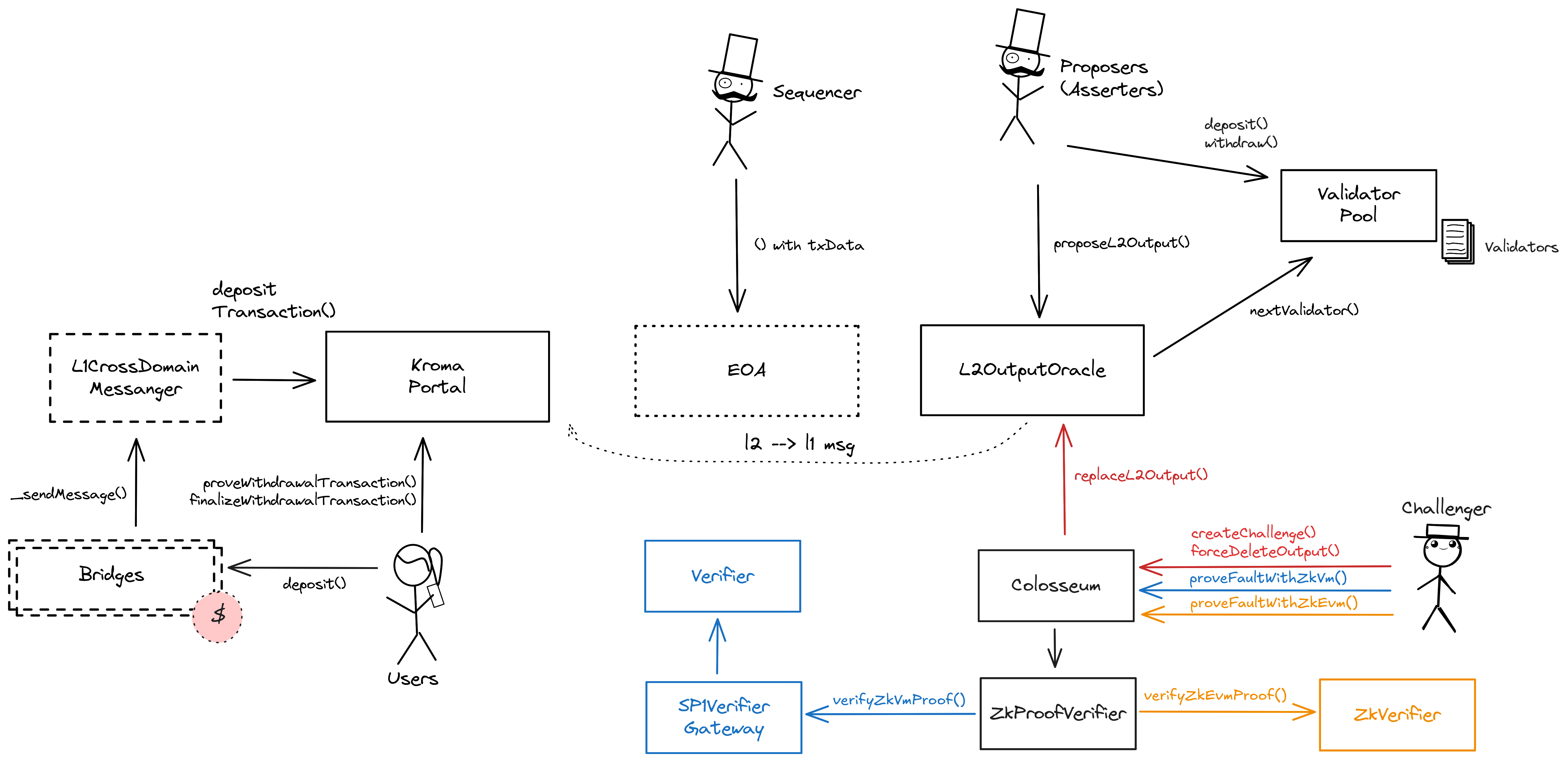
Kroma uses an interactive fraud proof system to find a single block of disagreement, which is then ZK proven. Once the single block of disagreement is found, the challenger is required to present a ZK proof of the fraud. This can be either a proof verified in a zkEVM verifier base on Scroll, or in a zkVM verifier built by Succinct SP1. If the proof is validated, the incorrect state output is deleted. The Security Council can always override the result of the challenge, it can also delete any L2 state root at any time. The protocol can fail under certain conditions.
Funds can be lost if the cryptography is broken or implemented incorrectly.
The system has a centralized sequencer
While forcing transaction is open to anyone the system employs a privileged sequencer that has priority for submitting transaction batches and ordering transactions.
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force any transaction
Because the state of the system is based on transactions submitted on the underlying host chain and anyone can submit their transactions there it allows the users to circumvent censorship by interacting with the smart contract on the host chain directly.
Autonomous exit
Users can (eventually) exit the system by pushing the transaction on L1 and providing the corresponding state root. The only way to prevent such withdrawal is via an upgrade.
EVM compatible smart contracts are supported
OP stack chains are pursuing the EVM Equivalence model. No changes to smart contracts are required regardless of the language they are written in, i.e. anything deployed on L1 can be deployed on L2.

Ethereum
Roles:
Allowed to pause withdrawals. In op stack systems with a proof system, the Guardian can also blacklist dispute games and set the respected game type (permissioned / permissionless).
Allowed to commit transactions from the current layer to the host chain.
Actors:
A soulbound token implementation to identify participants of the KromaSecurityCouncil. Owners of the token are members of the council. There are currently 10 members.
- Can upgrade with no delay
- ZKProofVerifier UpgradeGovernor → Timelock → ProxyAdmin
- L2OutputOracle UpgradeGovernor → Timelock → ProxyAdmin
- Timelock UpgradeGovernor → Timelock → ProxyAdmin
- ValidatorManager UpgradeGovernor → Timelock → ProxyAdmin
- KromaPortal UpgradeGovernor → Timelock → ProxyAdmin
- SystemConfig UpgradeGovernor → Timelock → ProxyAdmin
- KromaSecurityCouncil UpgradeGovernor → Timelock → ProxyAdmin
- L1CrossDomainMessenger UpgradeGovernor → Timelock → ProxyAdmin
- L1ERC721Bridge UpgradeGovernor → Timelock → ProxyAdmin
- ZkVerifier UpgradeGovernor → Timelock → ProxyAdmin
- Colosseum UpgradeGovernor → Timelock → ProxyAdmin
- USDCBridge UpgradeGovernor → Timelock
- L1StandardBridge UpgradeGovernor → Timelock → ProxyAdmin
- AssetManager UpgradeGovernor → Timelock → ProxyAdmin
- UpgradeGovernor UpgradeGovernor → Timelock → ProxyAdmin
- SecurityCouncilTokenOwners UpgradeGovernor → Timelock → ProxyAdmin
- ValidatorPool UpgradeGovernor → Timelock → ProxyAdmin
- Can interact with Timelock
- cancel queued transactions UpgradeGovernor
- execute transactions that are ready UpgradeGovernor
- manage all access control roles and change the minimum delay UpgradeGovernor → Timelock - or UpgradeGovernor
- propose transactions UpgradeGovernor
- Can interact with SystemConfig
Custom Multisig contract in which each signer is identified by a token. The threshold is 8 and the token contract is called SecurityCouncilToken.
- Can interact with Colosseum
- dismiss ongoing challenges and override state roots (
forceDeleteOutput())
- dismiss ongoing challenges and override state roots (
- Can interact with ValidatorPool
- become a validator without posting a bond
- A Guardian - acting directly
A Multisig with 3/5 threshold. Escrows a pool of KRO used as validator rewards by the AssetManager.
- A Sequencer - acting directly
- Can interact with SecurityCouncilTokenOwners
- one of the signers of the KromaSecurityCouncil
Arbitrum One
Actors:
Base Chain
Actors:

Ethereum
Sends messages from host chain to this chain, and relays messages back onto host chain. In the event that a message sent from host chain to this chain is rejected for exceeding this chain’s epoch gas limit, it can be resubmitted via this contract’s replay function.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
Used to bridge ERC-721 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
The main entry point to deposit ERC20 tokens from host chain to this chain.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
- This contract can store any token.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
The L2OutputOracle contract contains a list of proposed state roots which Proposers assert to be a result of block execution. Anyone can participate as a Proposer by depositing in the ValidatorPool. A root can be proposed every 1800 blocks (2s block time).
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
A standard timelock with access control. The current minimum delay is 0s.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
- canceller: UpgradeGovernor; ultimately SecurityCouncilTokenOwners
- executor: UpgradeGovernor; ultimately SecurityCouncilTokenOwners
- proposer: UpgradeGovernor; ultimately SecurityCouncilTokenOwners
- timelockAdmin: Timelock, UpgradeGovernor; ultimately SecurityCouncilTokenOwners
Manages the set of Proposers (Validators in Kroma) and selects the next proposer with the window to submit the output root within 30m, after which anyone can propose for them. It is also the entry point for other contracts, such as the L2OutputOracle and the Colosseum, which distribute output rewards and slash challenge losers. It makes successive calls to the AssetManager to apply changes to the proposers’ assets.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
This is a fork of the standard OP stack OptimismPortal contract, the main entry point to deposit funds from L1 to L2. It also allows to prove and finalize withdrawals.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
- guardian: KromaSecurityCouncil
- This contract stores the following tokens: ETH.
Merkle Trie contract used to prove withdrawals that were initiated in the legacy system, deprecated for new withdrawals and succeeded by a merkle tree library in the KromaPortal.
- Roles:
- owner: Timelock
Contract used to challenge state roots and prove fraud. If successful, the wrong state root in the L2OutputOracle is replaced.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
- security_council: KromaSecurityCouncil
- Roles:
- admin: Timelock; ultimately SecurityCouncilTokenOwners
- This contract stores the following tokens: USDC.
Manages the delegation and undelegation of KRO tokens and Kroma Guardian House (KGH) NFTs for Proposers (Kroma Validators) and distributes rewards.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
A governance proxy contract using token voting with SecurityCouncilTokenOwners as identification of actors allowed to vote/sign a proposal which is passed to the Timelock afterwards.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
- token: SecurityCouncilTokenOwners
Contract used to manage the Proposers. Anyone can submit a deposit and bond to a state root, or create a challenge. It also manages the Proposer rotation for each submittable block using a random selection. If the selected proposer fails to publish a root within 30m then the submission becomes open to everyone.
- Roles:
- admin: ProxyAdmin; ultimately SecurityCouncilTokenOwners
- security_council: KromaSecurityCouncil
Arbitrum One
Base Chain
Value Secured is calculated based on these smart contracts and tokens:
Main entry point for users depositing ERC20 tokens that do not require custom gateway.
Main entry point for users depositing ETH.
Main entry point for users depositing USDC.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).