Search
Search for projects by name
 L2.Finance-zk
L2.Finance-zk
Badges
About
Celer's Layer2.finance in ZK proofs Mode Built with StarkEx from StarkWare.
About
Celer's Layer2.finance in ZK proofs Mode Built with StarkEx from StarkWare.
Funds can be stolen if
Funds can be lost if
Users can be censored if
MEV can be extracted if
STARKs are zero knowledge proofs that ensure state correctness.
Proof construction relies fully on data that is NOT published onchain. There exists a Data Availability Committee (DAC) that is tasked with protecting and supplying the data.
There is no window for users to exit in case of an unwanted regular upgrade since contracts are instantly upgradable.
Users are able to trustlessly exit by submitting a Merkle proof of funds.
Data is not stored on chain
The balances of the users are not published onchain, but rather sent to external trusted parties, also known as committee members. A state update is valid and accepted onchain only if at least a quorum of the committee members sign a state update.
Funds can be lost if the external data becomes unavailable (CRITICAL).
Users can be censored if the committee restricts their access to the external data.
Each update to the system state must be accompanied by a ZK proof that ensures that the new state was derived by correctly applying a series of valid user transactions to the previous state. These proofs are then verified on Ethereum by a smart contract. The system state is represented using Merkle roots.
The system has a centralized operator
MEV can be extracted if the operator exploits their centralized position and frontruns user transactions.
Users can force exit the system
Force exit allows the users to escape censorship by withdrawing their funds. The system allows users to force the withdrawal of funds by submitting a request directly to the contract onchain. The request must be served within a defined time period. If this does not happen, the system will halt regular operation and permit trustless withdrawal of funds.
Users can be censored if the operator refuses to include their transactions. However, there exists a mechanism to independently exit the system.
Forced exit
If the user experiences censorship from the operator with regular exit they can submit their withdrawal requests directly on L1. The system is then obliged to service this request. Once the force operation is submitted and if the request is serviced, the operation follows the flow of a regular exit.
Emergency exit
If the enough time deadline passes and the forced exit is still ignored the user can put the system into a frozen state, disallowing further state updates. In that case everybody can withdraw by submitting a merkle proof of their funds with their L1 transaction.
Ethereum
Actors:
Can upgrade implementation of the system, potentially gaining access to all funds stored in the bridge. Currently there is no delay before the upgrade, so the users will not have time to migrate.
There exists a Data Availability Committee with unknown members and an unverified smart contract.
Can upgrade implementation of SHARP Verifier, potentially with code approving fraudulent state. Currently there is no delay before the upgrade, so the users will not have time to migrate.
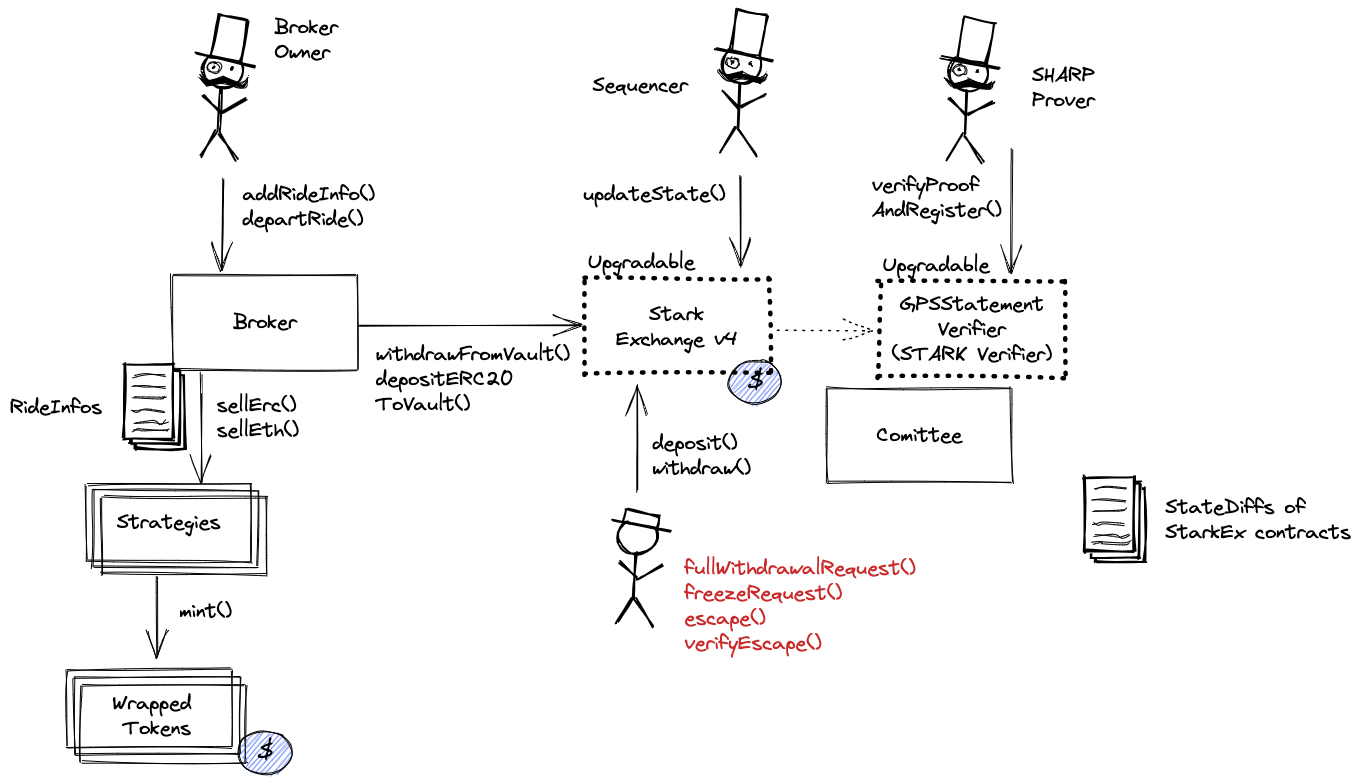
Most Broker functionality is restricted only for the owner, it includes managing rides, setting prices or slippages, burning shares.
Most Broker functionality is restricted only for the owner, it includes managing rides, setting prices or slippages, burning shares.

Ethereum
This contract stores the following tokens: ETH, USDC, USDT.
The source code of this contract is not verified on Etherscan.
Broker manages investment strategies on L1 for tokens deposited to the system. Strategies invest in specific protocols, e.g. Compound and they escrow LP tokens as custom Wrapped tokens.
It is through this contract that groups of users interact with the Compound DeFi protocol.
CallProxy for GpsStatementVerifier.
Starkware SHARP verifier used collectively by Starknet, Sorare, ImmutableX, Apex, Myria, rhino.fi and Canvas Connect. It receives STARK proofs from the Prover attesting to the integrity of the Execution Trace of these Programs including correctly computed state root which is part of the Program Output.
MemoryPageFactRegistry is one of the many contracts used by SHARP verifier. This one is important as it registers all necessary onchain data.
The current deployment carries some associated risks:
Funds can be stolen if a contract receives a malicious code upgrade. There is no delay on code upgrades (CRITICAL).
Funds can be stolen if the source code of unverified contracts contains malicious code (CRITICAL).